ColdFusion directory traversal FAQ (CVE-2010-2861)
A new Adobe hotfix for ColdFusion has been released recently. The vulnerability which was discovered by Richard Brain, was rated as important by Adobe and could affect a large number of Internet-facing web servers. The FAQ bellow is meant to shed some light on this vulnerability so that ColdFusion administrators can understand what they're up against.
The FAQ
Finally, by producing this FAQ I will attempt to explain why (at least on certain setups) this vulnerability should have been granted a CRITICAL rating by Adobe, rather than Important. As we'll see bellow, it is possible to fully compromise the underlying OS of a vulnerable ColdFusion server by exploiting this directory traversal vulnerability.
How does the vulnerability work?
The vulnerability is a variation of a classic directory traversal vulnerability, also referred to as arbitrary file retrieval. The attack involves tricking a server-side script to provide the contents of a file that it was not originally supposed to be made available. By moving up a few directory levels, the attacker is able to obtain the contents of files outside the application server's webroot via special strings such as ../. More information can be found on the OWASP website.
Is authentication required to exploit this vulnerability?
NO. The attacker doesn't require knowledge of any passwords in order to exploit the directory traversal bug.
What's the goal of the attacker when exploiting this vulnerability?
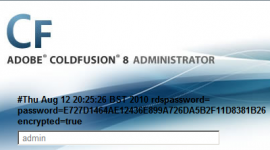
Just as any other type of directory traversal vulnerability, the attacker would usually attempt to obtain source code of the target site in order to identify security vulneraibilities. Additionally, the attacker would most likely attempt to obtain configuration files containing sensitive information. For instance, in the case of ColdFusion the attacker would most likely attempt to read the contents of neo-security.xml and password.properties. These configuration files contain database connection credentials and the ColdFusion administrator password respectively. Depending on how password.properties has been setup, the ColdFusion admin password will be hashed or stored in clear-text (encrypted=false).
What's the worst that could happen once this vulnerability has been exploited successfully?
As we'll see at the end of this post, once the attacker has gained access to the CF admin console - e.g.: by cracking the admin password - it might be possible to fully compromise the underlying OS.
How can the vulnerability be resolved?
You can either apply Adobe's patch or restrict access to the following directories and file from trusted IP addresses only: /CFIDE/adminapi/ /CFIDE/administrator/ /CFIDE/componentutils/ /CFIDE/wizards/ /CFIDE/install.cfm
What are the mitigating factors?
This vulnerability cannot be exploited on ColdFusion 9.X when default settings are used, unless of course you figure out a way to get around the directory traversal signatures used by the filtering routines. Additionally, the ColdFusion administrator login console must be available to the attacker. It is however quite common to find CF admin consoles directly available on the Internet.
If a long and sufficiently random admin password is used, cracking the SHA1 hash could prove to be difficult. This is applicable to CF MX7, 8 and 9 (see UPDATE notes). Version 6 doesn't hash the password, but instead encrypts it using a proprietary algorithm.
What versions of ColdFusion are affected?
According to the Adobe bulletin the affected versions are "ColdFusion 8.0, 8.0.1, 9.0, 9.0.1 and earlier versions for Windows, Macintosh and UNIX". However, due to time constraints I have only personally confirmed the vulnerability on version 8.0.1 under Windows.
Can you provide the actual exploit?
No. ProCheckUp will provide the exploit details at a later date. Although Richard Brain privately shared POC URLs with me, I will not make them available. Exploit details were only provided to me as a trusted security analyst for purpose of assessing the impact of the vulnerability and help me write this FAQ in the hope that it will benefit the community.
UPDATE: the exploit details were published by an anonymous researcher on 14/08/2010_, probably worked out by reverse-engineering Adobe's patches. ProCheckUp has also released the exploit details as of _17/08/2010.
Can you describe a real attack scenario?
The following a real attack scenario against ColdFusion 8 on a Windows server:
- Attacker confirms ColdFusion admin console is Internet facing. E.g.
http://target-domain.foo/CFIDE/administrator/index.cfm - Attacker exploits directory traversal vulnerability and obtains the contents of
C:\ColdFusion8\lib\password.properties, which contains the ColdFusion admin password - If the admin password was stored encrypted (actually CF8 hashes the admin password using the SHA1 algorithm, similar to CF MX7), the attacker then attempts to crack it via an offline password cracking attack or rainbow table lookup. Note that the default setting in ColdFusion 8 is
encrypted=trueas perpassword.propertiesfile. Otherwise, if the password is stored unencrypted (encrypted=false), there would be no need for password cracking. - UPDATE: as suggested by Niels Teusink, an attacker could login as the CF administrator without needing to crack the SHA1 hash. I verified his observation and can confirm it works well. You can follow these steps (tested on Firefox 3.6.8) to login using the SHA1 hash. i.e.: no need to crack the password hash:
1. Configure your favorite MITM proxy - e.g. [Burp](http://portswigger.net/proxy/) - to capture traffic between your browser and target CF admin console- Enter hash in password field of login form (usually located on
/CFIDE/administrator/enter.cfm) - Type the following on your browser's address bar and press enter (make sure JavaScript is enabled on your browser):
javascript:hex_hmac_sha1(document.loginform.salt.value,document.loginform.cfadminPassword.value) - Record value. e.g.
AFA9C9D917916DE6CE05C1BFEC0470E07A246CB0 - Press browser's Back button
- Press Login on the login form (trapping/intercept mode should be enabled on your MITM proxy at this point)
- Trap the login request and replace the value of the
cfadminPasswordparameter with the value recorded above - Forward request
- Enter hash in password field of login form (usually located on
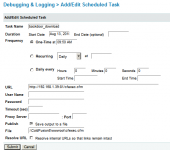
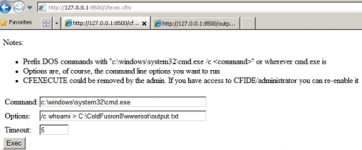
- At this point, the attacker would be able to login as a CF admin and upload a malicious CFM script that would allow him to run remote commands (SYSTEM privileges by default). Uploading files to a CF server via the administrator console is a bit counter-intuitive. The attacker would basically add a scheduled task that would download cfexec.cfm to the server's webroot
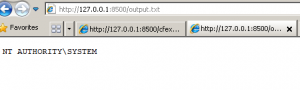
- At this point, the attacker has gained full control of the underlying Windows OS as the CF service runs with SYSTEM privileges by default
If the CF admin password is hashed and the attacker is unable to crack it, he could always try to obtain the database connection credentials (C:\ColdFusion8\lib\neo-datasource.xml) which can be easily decrypted and then directly authenticate to the backend DB server. This however wouldn't normally be possible on a firewalled environment where the back-end DB server is not directly exposed to the Internet. Network access controls are your friends!
Post Updates
- 16/09/2010 - new path added as part of blacklisting solution
- 16/09/2010 - added trick to login without cracking the CF admin password hash
- 16/09/2010 - mentioned recently published exploit code for the CF traversal vulnerability
- 18/09/2010 - fixed typos and mentioned release of exploit details by ProCheckUp
Archived Comments
onSubmit="cfadminPassword.value = hex_hmac_sha1(salt.value, hex_sha1(cfadminPassword.value));"
This allows attackers to authenticate using the hash instead of cracking it.del \ColdFusion8\wwwroot\cfexec.cfm<Location /CFIDE>
Order Deny,Allow
Deny from all
Allow from 127.0.0.1
</Location>